About Zer0Con
Zer0Con is POC’s ‘CLOSED’ international security conference. It focuses on finding, analyzing, and exploiting vulnerabilities. Zer0Con aims to have high-level technical presentations.
∙ It is a high-level and closed conference.
∙ It only focuses on finding, analyzing, exploiting vulnerabilities.
∙ Only speakers, attendees, and sponsors will share vulnerabilities information.
∙ Zer0Con attendees can share various information and establish unique community.
∙ Training courses also focus on finding, analyzing, exploiting vulnerabilities.
∙ If you have certain level of ability to find bugs and make exploit code, you will improve yourself through Zer0Con.
* 가상화 시스템 exploitation
* Blockchain exploitation
* S사 스마트폰 exploitation
* WIFI exploitation
* Bluetooth Exploitation
* Windows Kernel exploitation
* L사 방화벽 exploitation
* 모든 Android 디바이스들에 적용되는 type confusion 커널 취약점을 이용해 universal Android rooting을 구현하는 기술
* Chrome renderer exploitation
April 11, 2019
|
TIME |
SPEAKER |
TITLE |
|
09:00 ~ 09:30 |
Registration |
|
|
09:30 ~ 10:00 |
Welcome & Introduction |
|
|
10:00 ~ 11:00 |
Eloi Sanfelix |
TEE Exploitation by example: exploiting Trusted Apps in Samsung's TEE |
|
11:00 ~ 11:20 |
Break Time |
|
|
11:20 ~ 12:20 |
WANG, YONG |
From zero to root: Building universal Android rooting with a type confusion vulnerability |
|
12:20 ~ 13:20 |
Lunch |
|
|
13:20 ~ 14:20 |
Maor Shwartz |
Selling 0-days to governments and offensive security companies |
|
14:20 ~ 14:30 |
Break Time |
|
|
14:30 ~ 15:30 |
Marco Grassi Kira |
Vulnerability Discovery and Exploitation of Virtualization Solutions for Cloud Computing and Desktops |
|
15:30 ~ 16:20 |
Social Break |
|
|
16:20 ~ 17:20 |
Park Jinbum |
Leak kernel pointer by exploiting uninitialized uses in Linux kernel |
|
17:20 ~ 17:30 |
Break Time |
|
|
17:30 ~ 18:30 |
Zhiniang Peng Yuki Chen |
All roads lead to Rome Many ways to double spend your cryptocurrency |
April 12, 2019
|
TIME |
SPEAKER |
TITLE |
|
10:00 ~ 11:00 |
Sergey Ivanov |
Getting RCE in Personal Security Products from scratch |
|
11:00 ~ 11:30 |
Break Time |
|
|
11:30 ~ 12:30 |
Nikita Tarakanov |
Exploiting Kernel Memory Corruptions on Microsoft Windows 10 19H1 |
|
12:30 ~ 14:00 |
Lunch |
|
|
|
(TBA) |
|
|
|
|
|
|
14:00 ~ 15:00 |
Denis Selanin |
Researching Marvell Avastar Wi-Fi: from zero knowledge to over-the-air zero-touch RCE |
|
15:00 ~ 16:00 |
Social Break |
|
|
16:00 ~ 17:00 |
Wen Xu Soyeon Park |
Comprehensive Browser Fuzzing: From DOM to JS |
|
17:00 ~ 17:30 |
Break Time |
|
|
17:30 ~ 18:30 |
Stephen Röttger |
A guided tour through Chrome's javascript compiler |
|
19:00 ~ |
Dinner Party for Speaker, All Attendees |
|
[Day 1]
1. TEE Exploitation by example: exploiting Trusted Apps in Samsung's TEE
Brief biography
Eloi works as a Security Researcher at Blue Frost Security, where he focuses on vulnerability research and exploitation on Android platforms.
In the past, he spent 9 years performing security evaluations of smart cards and embedded systems. This included analysis from the silicon layer up to the software layer. During this period, he gained experience in auditing the hardware and software side of Trusted Execution Environments.
Abstract
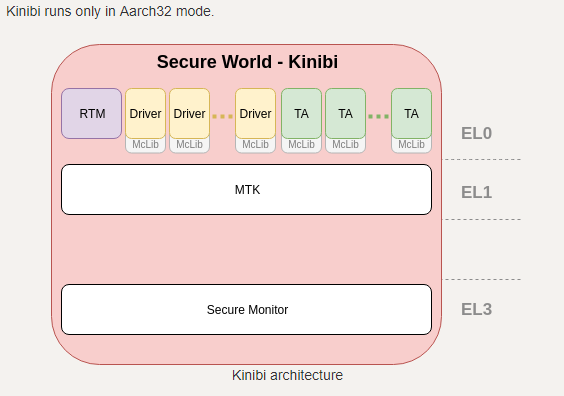
We first provide a small introduction to what TEEs are and how TrustZone is used to support a TEE. We follow up with introducing the Kinibi OS and explaining how to start reversing and bug hunting on Kinibi TAs and TDs.
Next, we focus on three types of vulnerabilities Finally, we look into post-exploitation opportunities after compromising a Trusted Application. For this we present the API between TAs and TDs and zoom into how we exploited SVE-2018-12881 to compromise the Linux kernel and the RKP hypervisor.
독일오펜시브 컨퍼런스 OffensiveCon을 운영하는 BlueFrost 연구원 Eloi Sanfelix의‘TEE Exploitation by example: exploiting Trusted Apps in Samsung’s TEE’ 발표가 있다. 그는 TEE(Trusted Execution Environment)와 TrustZone에 대한 설명과 함께 Kinibi OS 소개 후, 신뢰 애플리케이션에 존재하는 취약점 및 익스플로잇테이션에 대해 설명한다. Trustonic사의 Kinibi는 대표적인 안드로이드 주요 TEE 운영체제 중 하나로 이미 삼성, LG, Vivo, 샤오미 등 디바이스들에 탑재되어 있다.
TEE (Trusted Execution Environment) : hardware 기반이어야 하며, samsung의 경우 knox로 만들어짐
TA (Trusted Application)
TD (Trusted Devices???)
*** Trust Issue : Exploiting TrustZone TEEs (https://googleprojectzero.blogspot.com/2017/07/trust-issues-exploiting-trustzone-tees.html)
TrustZone이란? (https://since2018.tistory.com/17)
TEE 기술 소개 및 활용 방안 ( http://www.t-town.co.kr:8080/images/Event/2014tech/4_tmonet_teeskill.pdf)
블록체인 - 하드웨어보안활용 TEE? (https://steemit.com/tee/@sshong3/tee)
KNOX 워런티 개념 및 기능 (https://m.blog.naver.com/PostView.nhn?blogId=mutantcell&logNo=203794743&proxyReferer=https%3A%2F%2Fwww.google.com%2F)
KINIBI TEE : Trusted Application Exploitation (https://www.synacktiv.com/posts/exploit/kinibi-tee-trusted-application-exploitation.html)

2. From zero to root: Building universal Android rooting with a type confusion vulnerability
Brief biography
WANG, YONG(@ThomasKing2014) is a security researcher of Alibaba Security, currently focusing on Android and Browser vulnerability hunting and exploitation. These years he has reported several vulnerabilities in Android system core components and kernel, which were credited in multiple advisories.
Abstract
With more strict SELinux policies and mitigations, Android rooting is becoming an "impossible" challenge. In this talk, I will first introduce a type confusion kernel bug I found last year, which affects all the Android devices. Since the affected slab caches are all dedicated, I will detail how to shape Heap Fengshui and convert it to a Use-After-Free vulnerability.
Next, I will detail how to leverage the freed objects and bypass KASLR/PXN/PAN mitigations effectively. Android 9 introduces KCFI mitigation. In reality, some Android vendors have had implemented the KCFI mitigation on their Android 8 devices. To build the universal Android rooting solution, I will detail their KCFI implementation, how to bypass it and gain the root privilege.
중국 알리바바(Alibaba) 보안팀 연구원인 Wang Yong의 ‘WZRooter: Building universal Android rooting with a type confusion vulnerability’도 있다. SELinux(리눅스 보안 강화 커널)로 인해 루팅이 어려워진 상황에서 발표자는 모든 안드로이드 기기에 영향을 미치는 type confusion 취약점을 이용해 임의 커널 메모리 읽기/쓰기 능력과 루트 권한을 얻고, 보호 기법들을 우회하는 방법을 상세히 설명한다. 새로운 보호 기법 KCFI(커널제어 흐름 무결성)이 적용된 Android9에서도 동일한 공격이 가능함을 보여줄 예정이다.
SELinux 관련 유용한 페이지 ( https://www.linux.co.kr/home2/board/subbs/board.php?bo_table=lecture&wr_id=1193)
Control Flow Integrity in the Android Kernel (https://android-developers.googleblog.com/2018/10/control-flow-integrity-in-android-kernel.html)
KCFI ( https://source.android.com/devices/tech/debug/kcfi)
Android : protecting the kernel (https://events.static.linuxfound.org/sites/events/files/slides/Android-%20protecting%20the%20kernel.pdf)
3. Selling 0-days to governments and offensive security companies
Brief biography
Maor Shwartz
Abstract Selling 0-days is a fascinating process that not a lot of people are familiar with.
In my presentation I will try to answer the following questions from 3 different angels (researcher/ broker/client).
Who (researcher profile) is selling 0-days to governments / offensive security companies?
What is the process of selling 0-days?
How to sell 0-days?
At the end of my presentation, I will give a few tips for researchers that want to sell 0-days to offensive security companies/governments.
기술적 발표 외에 제로데이 취약점 시장 관련 발표도 있다. Q-recon 보안 연구원인 MaorShwartz가 ‘Selling 0-days to governments and offensive security companies’라는 주제로,버그헌팅을 통해 찾은 제로데이를 보안 기업이나 정부에 파는 과정, 노하우 등 상세 내용을 발표한다. Zerodium(제로디움) 등 유명 제로데이 거래 업체 대표들도 참가할 예정이므로 관심 있는 참가자들은 네트워킹 시간을 활용해 자유롭게 접촉할 수 있다.
4. Vulnerability Discovery and Exploitation of Virtualization Solutions for Cloud Computing and Desktops
Brief biography
Marco Grassi(@marcograss) is currently a Senior Security Researcher of the KeenLab of Tencent (previously known as Keen Team). He is part of the team that won the ""Mobile Master of Pwn"" title in Tokyo for Mobile Pwn2Own 2016, working on iOS. He was also one of the main contributors at Desktop Pwn2Own 2016 for the Safari target with sandbox escape to root. He is a member of the team who won the title of ""Master Of Pwn"" at Pwn2Own 2016. He found a VMWare escape at Desktop pwn2own 2017, and baseband RCE and wifi iOS at Mobile pwn2own 2017 where we were awarded ""Master Of Pwn"" for the third time. He has spoken at several international security conferences such as Black Hat USA, DEF CON, Infiltrate, CanSecWest, ZeroNights, Codegate, HITB and ShakaCon.
Kira(Xingyu Chen) is a senior student at Zhejiang University, also an intern at Tencent Keenlab. He has a lot of interests in security fields, virtualization in particular. He plays CTF in team AAA ( sometimes A*0*E ), which participated in DEFCON 25 & 26. He has made a VirtualBox escape ( together with Marco Grassi ) and a QEMU escape.
Abstract
In our talk we will first give you a overview of the virtualization solutions, and their attack surface.
Then we will first switch to VirtualBox, explaining the architecture and attack surface, and showing a VM escape.
After that we will focus on QEMU, discussing a VM escape from QEMU, both the bug and the exploitation.
중국 Tencent KeenLab의 Marco Grassi와 Xingyu Chen(Kira)가 ‘Vulnerability Discov-ery and Exploitation of Virtualization Solutions for Cloud Computing and Desk-tops’ 발표를 통해 VMWare, VirtualBox 등의 제로데이 취약점들을 익스플로잇하는 기술을 선보일 예정이다.
5. Leak kernel pointer by exploiting uninitialized uses in Linux kernel
Brief biography
Park Jinbum has been working at Samsung Research, Security Team. He focuses on developing security solution, writing an academic paper on system security, in particular, kernel security, side channel attack/defense, hw-assisted secure platform such as TrustZone, Hypervisor. and He enjoys to spend a time to bring something new and novel methods for finding and exploiting vulnerabilities.
Abstract
If an attacker want to construct full exploit chain against linux kernel, He first should find a way to bypass KASLR.
The one way to bypass it is information leak caused by carefully exploiting uninitialized use vulnerability. In this presentation, I'll introduce KptrTools that is the set of tools to exploit the vulnerability, next I'll show you how an exploit developer can make a perfect exploit with the KptrTools.
삼성 국내 보안 연구팀 소속인 박진범 연구원의 ‘Leak kernel pointer by exploiting uninitialized uses in Linux kernel’ 발표도 있다. 리눅스 커널 풀체인 익스플로잇을 위해 KASLR을 우회하는 방법과 KptrTool들을 사용해 취약점을 익스플로잇하는 방법에 대해 소개한다.
발표자 블로그*** Lifting the (Hyper) Visor : Bypassing Samsung's Real-Time kernel Protection (by Bal Beniamini) ( http://blog.daum.net/tlos6733/186)
:) Mitigation #1 - KASLR
- ROP 를 통해 원하는 코드 부르려면, 일단 코드 주소 알아야만 하므로, KASLR 우회해야 함.
- KNOX 에 포함된 KASLR 은, 하나의 single "slide" 값에 따라 커널 주소가 확정되는 것. 즉, 하나의 포인터만 유출되더라도 다른 주소 알 수 있음.
- 이러한 약점에 대한 하드닝으로 리눅스 커널은 "%pK" 라는 특수한 specifier 를 만듬.
이는, kptr_restrict 값에 따라, 출력을 다르게 하는 방법인데, 이 값이 kptr 출력을 허용하는 설정이면. (이 값은 당연히 커널에 있는 값)
%pK 에서 주소값이 출력되고, 그게 아니면 주소값이 출력 안되는 것.
- Galaxy S7 Edge 에서 이를 우회할 때 사용하는 취약점은 [4].
%pK 대신에 어떤 개발자의 오타(?)가 발생해서, %pk 가 들어간 것!!
/* seq_printf(s, " %pk(%s:%d): %d\n", */
%pk 는 kptr_restrict 설정에 영향 받지 않고, 항상 포인터 값을 leak 하는 것!!
KASLR 자체를 약간 이상하게 만들어 놓은 부분. 개발자의 실수 확률이 엄청 높도록 만들어놓았음.
이걸로 pm_qos 의 contents 를 읽을 수 있고, 여기서 포인터 값을 추출하면! KASLR slide 값 알아낼 수 있다.
6. All roads lead to Rome Many ways to double spend your cryptocurrency
Brief biography
Dr. Zhiniang Peng is a security researcher at Qihoo 360 core security. He has over 10 years of experience in both offensive and defensive security and published many academic papers in the field of information security. Dr. Peng has designed several security products in data security and discovered several critical vulnerabilities in various fields. His current research interests include software security and applied cryptography.
Yuki Chen is a member of 360 Vulcan Team. He has over 9 years experience in the security industry and currently works as the director of a vulnerability research group at Qihoo 360. He is mostly interested in vulnerability hunting and analyzing and exploit development. He has discovered and exploited vulnerabilities in a wide range of products including IE, Edge, Safari, FireFox, Adobe flash/pdf, Java, block chain software and so on. He has spoken at several security conferences such as BlackHat EU, SysCan, 44Con, HitCon, PacSec, SysCan360 and XCon.
Abstract
Bitcoin has been developed for ten years, and since then countless digital currencies have been created. But the discussion of double-spend attacks seems to still concentrate on 51% Attacks. In fact, our research has found that there are many other ways to achieve double-spend attacks, we got more than USD 300K+ bounty from the vedor for reporting these new bugs resulting double-spend. In this presentation, by intruducing a number of double-spend attack vulnerabilities that we have foud in EOS, NEO, ONT and other large blockchain paltforms, we summarized various reasons for causing double-spend attacks.
세계적인 취약점 연구자인 중국 치후360 보안 연구원인 Yuki Chen과 Zhiniang Peng은 이 발표에서 EOS, NEO, ONT등 주요 블록체인 플랫폼에서 발견한 double-spend 취약점들에 대해 상세히 설명할 계획이다.
[Day 2]
1. Getting RCE in Personal Security Products from scratch
Brief biography
Sergey Ivanov
Abstract
During recent years, OS vendors efforts in introducing new mitigations, as well as improved code quality, leads to raising the bar to find a reliable & remotely exploitable vulnerability in OS components. At the same time, Personal Security Products (or commonly called Anti-Viruses to HIPS) still present on a majority of desktops and have high-level capabilities; moreover without user request, they scan emails, content on shared folders, and web pages. This creates a perfect target for an attack.
I want to show, using as the example Kaspersky Anti-Virus, how to discovery a vulnerability in the emulator. Apply several approaches to effectively fuzz and reverse engineering internals of the AV engine. And finally, gain RCE via a web browser without users interaction.
2. Exploiting Kernel Memory Corruptions on Microsoft Windows 10 19H1.
Brief biography
Nikita Tarakanov
Abstract
Each new version of Windows OS Microsoft enhances security by adding security mitigation mechanisms - Kernel land vulnerabilities are getting more and more valuable these days. For example, the easy way to escape from a sandbox is by using a kernel vulnerability. That's why Microsoft struggles to enhance security of Windows kernel.
Kernel pool allocator plays a significant role in security of whole kernel. Since Windows 7, Microsoft started to enhance the security of the Windows kernel pool allocator. In Windows 8, Microsoft has eliminated almost all reliable (previously published) techniques of exploiting kernel pool corruptions.
Then Microsoft eliminated "0xBAD0B0B0" technique in Windows 8.1, and there was no easy technique to exploit Pool Overflows on Windows 8.1
Then DKOM/DKOHM technique was present that gave really nice primitives(arbitrary read/write/execute) for kernel exploitation.
Following up Microsoft obfuscated TypeIndex in an object header leaving DKOM/DKOHM technique useless. But Microsoft left unprotected optional headers that gave born to DKOOHM technique.
Sadly enough, Microsoft introduced brand new Kernel Memory Allocator on Windows 10 RS5 leaving current pool memory manipulation techniques useless. Also Microsoft has been eliminating various techniques of exploiting arbitrary kernel memory corruptions: changing layout of GDI/USER objects, Pool Memory Isolation etc.
Plus to that Microsoft has been implementing various generic exploit mitigations: SMEP, kCFG, HVCI and finally SMAP on 19H1.
This talk is about the complexity of development Kernel Memory Corruption exploits on the brand new Windows 10 19H1.
전 VUPEN 연구원이자 윈도우 커널 취약점 연구에 탁월한 Nikita Tarakanov가 ‘(In)Security in Windows on ARM’발표를 진행한다. 상세 내용은 발표자의 요청으로 비공개 상태이며, 곧 공지될 예정이다.
3. Researching Marvell Avastar Wi-Fi: from zero knowledge to over-the-air zero-touch RCE
Brief biography
Denis Selanin
Abstract
Last year, the cybersecurity community was wrapped up in the discussion about the vulnerability of Broadcom BCM43xx Wi-Fi chipsets. By exploiting the firmware vulnerability of these chipsets, researchers could develop exploits enabling them to gain access to a device without any need to interact with its user. Regardless of the degree to which the OS of a device was protected, in a system, there was a separate chip that was responsible for Wi-Fi frames parsing and operated with no anti-exploitation functionality. This talk will cover the internals and structure of the Marvell Avastar Wi-Fi chips. We will also discuss the techniques of detecting and exploiting firmware vulnerabilities, as well as the mechanisms and operation algorithms of the ThreadX real-time OS. ThreadX is the OS used as a basis for the firmware of these devices. The last topic addressed in this report will be the tools/techniques that simplify the process of analyzing devices of the kind.
임베디드 기기 보안 업체인 Embedi의 연구원 Denis Selanin은 ‘Researching Marvell Avastar Wi-Fi: from zero knowledge to over-the-air zero-touch RCE’ 주제로 발표한다. 해당 발표는 Marvell Avaster 와이파이 칩에 대한 상세 설명부터 펌웨어 취약점 탐지 및 익스플로잇 기술까지 포함하고 있다.
4. Comprehensive Browser Fuzzing: From DOM to JS
Brief biography
Wen Xu is a Ph.D. student in computer science at Georgia Tech, advised by Prof. Taesoo Kim. His research focuses on developing automatic systems for finding bugs in modern software. He holds the B.S. degree (2016) in computer science from Shanghai Jiao Tong University.
Soyeon Park is a Ph.D. student in computer science at Georgia Tech, advised by Prof. Taesoo Kim. Her research focuses on hardware-assisted security and finding bugs in modern software. She holds the B.S. degree (2017) in computer science and engineering from Pohang University of Science and Technology (POSTECH).
Abstract
From then till now, browsers have always been one of the most popular targets for attackers to compromise user clients. Due to the complexity of modern browsers, fuzzing is considered the most effective and practical approach to discover their security vulnerabilities. In recent years, researchers have proposed a number of fuzzers targeting DOM engines and JavaScript engines, which are two largest sources of browser bugs, and found thousands of security critical bugs. In this talk, we will summary the existing approaches of these fuzzers, point out their shortcomings and propose the design of our new fuzzers that improve the state-of-the-art techniques.
In the first half of our talk, we will focus on DOM fuzzing. Existing generation-based DOM fuzzers, such as domato developed by Google Project Zero, rely on static grammar rules and thereby the generated testcases suffer from runtime errors. We will propose a new generation-based DOM fuzzer which supports fuzzing various DOM components more effectively, including WebGL. We note that there is no past talk about WebGL fuzzing in browsers, which involves generating not only JS calls but also shader programs. Next, We will discuss JS fuzzing. Recently, a lot of JIT compiler bugs in JS are found and exploited in hacking events. However, there is no public JS fuzzer that specifically targets JIT compilation. Existing generation-based or mutation-based JS fuzzers, such as jsfunfuzz developed by Mozilla security team and IFuzzer all face many syntax and semantic errors, which are not suitable for JIT fuzzing. We will propose a new JS fuzzer which innovatively leverages JIT byte codes and reduce syntax and semantic errors to generate code based on our pre-defined rules. We will present several DOM and JS bugs we found in Edge, Safari and Chrome, and demonstrate how to exploit one Safari RCE bug on macOS regardless of the isolated heap introduced in 2018.
미국 조지아텍 연구원들의 브라우저 퍼징 발표도 확정되었다. 최근 많은 브라우저 연구자들은 상대적으로 취약한 DOM 엔진과 자바스크립트 엔진을 타깃으로 하는 퍼저들을 사용해왔다. 해당 발표에서는 DOM과 JS퍼징, 각각의 퍼저들을 살펴보고, Edge, Safari, Chrome에 존재하는 DOM과 JS취약점들을 소개한다. 더불어 macOS의 SafariRCE 제로데이버그 익스플로잇 시연도 공개된다.
5. A guided tour through Chrome's javascript compiler
Brief biography
Stephen Röttger(@_tsuro) is working on the Google security team working on a broad range of topics from production security, sandboxing and offensive security exercises to web security and browser vulnerability research. In his free time he's playing CTFs with Eat Sleep Pwn Repeat, qualified repeatedly for the DEF CON CTF and organizes the yearly CCC CTF.
Abstract
TurboFan is the optimizing compiler of Chrome's javascript engine V8. In this talk, I will explain the inner workings of the compiler and its optimization passes from the point of view of a vulnerability researcher. I will give an overview over common vulnerability patterns and guide you through all the steps from vulnerability discovery, the analysis workflow and exploitation using crbug.com/880207 as an example.
After we achieved code execution in the renderer, I will discuss the attack surface of the browser process and how site isolation comes into play.
'Conference' 카테고리의 다른 글
| POC 2019컨퍼런스 일정 및 발표주제 (0) | 2019.10.31 |
|---|---|
| AWS101 seminar 정리 (0) | 2019.10.31 |